Per UNT policy and best practices, we encrypt all CAS IT-managed laptops. Users with UNT laptops we do not maintain must also encrypt their laptops.
Encrypting information renders it near useless to thieves and protects our clients, students, employees, and intellectual properties because:
- Data, in the traditional plural and abstract sense, do not convey meaning.
- Information happens when data convey meaning to you, including confidential and/or sensitive stuff like:
- Clinic, donor, and student identities and related matter
- Employee identities and evaluations
- Proprietary secrets
- Encryption software enables you to mask information as data and unmask data into information
The processes outlined below only encrypt the internal hard drive and will not alter removable drives and cloud (server) drives--so continue to safeguard those items! Jump to:
Back to topDell PC (Windows)
Do the following to check drive encryption status:
- Press: Ctrl+Esc
- Type: C:
- Press: Enter
While encrypting, you should see a padlock on top of the drive icon and a red bar progress noting limited free space available, similar to the following: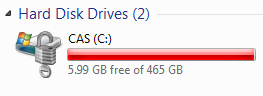 When done encrypting, you should see a padlock on top of the drive icon, similar to the following:
When done encrypting, you should see a padlock on top of the drive icon, similar to the following: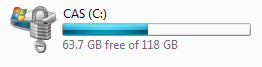
Enable Encryption
- Back-up all local, original work for all people who use this computer such as desktop files, bookmarks, "My Documents" files:
- Consider copying the data to a removable "thumb" or "flash memory" drive
- Consider trying out our new Windows back-up solution
- Secure your backed-up information from theft
- Bring your computer to campus on Wednesday
- Get all updates:
- Attach it to power because encrypting requires a lot of energy
- Attach it to the wired network so our systems can talk with each other
- Leave it running overnight and through Thursday so our systems can find, schedule, and update your computer (see notes below)
- By Friday, the system should work as noted in the next section.
Notes:
- Testing shows it takes six to twelve hours to encrypt an entire computer.
- Encryption requires a lot of processing so expect it to run very slowly during that time and use a lot of energy.
- Testing shows you may close the lid or "sleep" the computer at any time to pause the encrypting process. Upon awakening the computer, the encrypting process automatically resumes.
Use your encrypted computer
Once you enable encryption, the computer should work almost identically to the way it did previously, although just a tad more slowly. Our research showed that, without an additional PIN, encryption was practically useless and the technology does not currently allow the use of your current login and password (sigh). Therefore, you must learn the new PIN:
- Login to this web site
- Visit the PIN web page
When you close/open a laptop lid, the computer goes to "sleep," slipping into a very low (but still "on") power-consumption mode. Using the computer in this state remains the same. Sometimes, when you turn off the power or the battery runs out, you turn on the computer from an "off" state, and that's when you get the new boot process:
- Boot your computer as normal
- Enter your PIN (see above) at the following screen:

- Use your computer as normal
Resolve Problems
- Initially, the boot pin does not exist.
- If BitLocker doesn't enable via our automated processes, CAS ITS will need to enable it manually.
- Contact our office if you need help.
Mac (macOS)
Enable Encryption
While the risk of data loss while enabling encryption is very low, we discourage starting the process remotely, so that we can ensure that we have a recent backup of your data prior to the encryption process. We can however enable encryption remotely if you maintain your own backups.
You should:
- Contact our Service Desk to:
- Schedule a time to drop off your computer for a couple workdays.
- Back-up all locally-stored, original work.
- Bring your computer to GAB 313 with power cable
Once we have your computer, we will:
- Back it up as a courtesy (you remain responsible for local data!)
- Start the encryption process
Use your encrypted computer
Upon boot, the new login screen displays people who may unlock the computer and login like normal. Remember this: The next time you change your password, it may take 24 to 48 hours before your computer recognizes the change--just use the old password for the initial login screen and, if prompted again, use your new UNT password.
Resolve Problems
Getting Access When You Forget the Password
If you forget your password:
- Have another person (listed in the initial login screen) unlock the computer.
- Login to your account.
If that doesn't work, bring the computer to CAS IT and we can unlock it and enable you to use it again.
Back to topExceptions
In some cases, encryption may cause substantial harm or pose unsuitable risk.
For such cases:
- CAS IT may independently determine or the user should provide CAS IT with:
- Reason why encryption may pose substantial or unsuitable risk
- Asset number for every laptop that falls under that justification
- Exception term (e.g., until May 2017)
- If CAS IT staff agrees, CAS IT staff will submit a ticket to UNT System IT Security with the above information.
- If UNT System IT Security agrees, they will authorize CAS IT staff to implement the exception.

